How well prepared is the financial sector for DORA? What implementation challenges do those responsible need to be prepared for? And how can the reporting obligations of the regulation be fulfilled with the help of smart tools? Thorsten Breuer, Managing Partner (CEO) & Founder of Kolibri Advisory & Services GmbH i.G., and Robin Schmeisser, Managing Director of Fabasoft Contracts GmbH, discussed this in the Handelsblatt How To Business webinar "The countdown is on: Implementing DORA efficiently in the financial sector with digital management of IT service providers".
How well prepared are financial companies for DORA?
Even though the implementation deadline of January 17, 2025 is approaching, different levels of preparation can currently be seen in the industry. In principle, the financial industry is already subject to strict regulation (e.g. in Germany through MaRisk) and has therefore established good mechanisms for adapting to changes in the law. The larger the company and the higher the business frequency, the better prepared the companies would be in reality, says Thorsten Breuer.
Nevertheless, the expert still sees some catching up to do when it comes to cybersecurity. The reason for this is the lack of management of the dependencies resulting from the high degree of networking and the digital business models of financial companies. For example, cybersecurity has so far tended to be seen as a "mandatory topic" with little understanding and discussion outside the IT departments. This will inevitably change with the expansion of DORA's responsibilities.
Who is liable in the event of non-compliance with DORA requirements?
According to Breuer, there is currently a growing trend at EU level to make top management responsible for meeting regulatory requirements, see NIS2, among others. At DORA, too, cybersecurity is now a top priority. Non-compliance can result in severe sanctions. In addition to substantial fines, a breach of due diligence obligations can even lead to the suspension of managing directors and board members if, for example, the company does not pass the relevant annual audits. "The regulation also affects the main decision-makers on a personal level and thus ensures the necessary execution," adds Schmeisser.
What information must financial companies report under DORA?
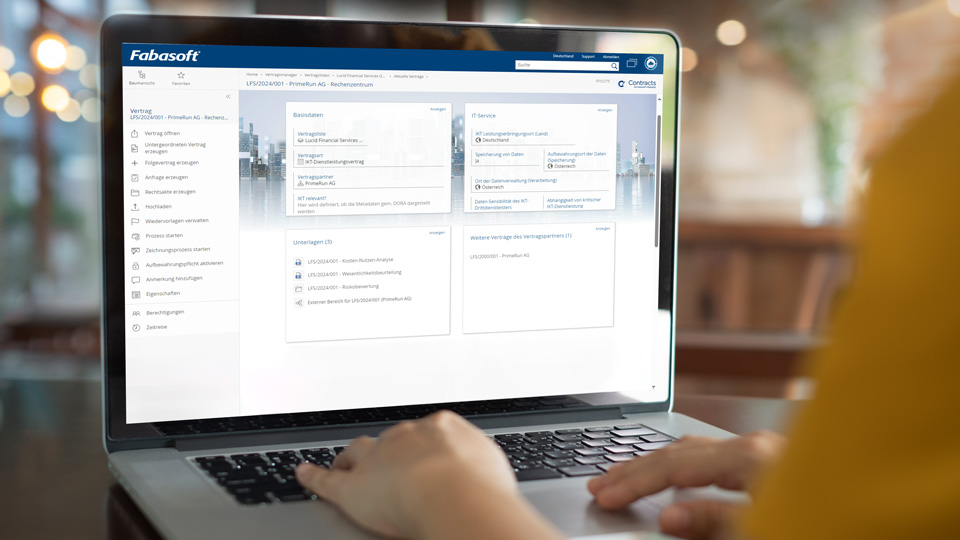
The management of ICT service providers is a key pillar of DORA. The EU regulation obliges financial companies to document all IT services procured completely and transparently in the form of an register of information. This relational data model must contain extensive information on suppliers and IT services, including all contracts and a wide range of certificates and checks such as due diligence, risk assessments and exit strategies. In addition to these already resource-intensive reporting obligations, there is also the problem of the high degree of overlap with the outsourcing register in accordance with the EBA guidelines (which will continue to have to be kept). "In this area of conflict, we see it as our responsibility as a service provider to avoid redundancy together with our customers," says Schmeisser. "On the one hand, to keep business processes efficient and, on the other, to pursue the goal of generating both registers from a single point of truth. This ensures that the content of the two reports remains congruent and that no different information reaches the authorities."
What impact does DORA have on ICT third-party provider management?
With regard to ICT third-party provider management, one focus of action is on monitoring and adapting outsourcing contracts to the regulatory requirements. Financial companies must review their entire contract portfolio with ICT third-party providers for compliance with DORA and conclude new supplementary agreements if necessary. This applies not only to "critical outsourcing" as defined in the EBA guidelines, but also to all IT service providers, which can mean several hundred contracts. If this control and revision process is carried out manually, it takes a considerable amount of time. Especially as in many cases it comes down to the mere details of the wording of individual clauses. An AI-based contract portfolio analysis provides a solution, as Schmeisser explains: "Fabasoft Dora's AI supports the control and analysis of the contract portfolio and thus the process of making the agreements DORA-compliant."
A second core aspect is setting up the necessary workflows within the company. Outsourcing processes are a cross-cutting issue that involves cooperation between a wide range of departments, from outsourcing/compliance management to the involvement of the CISO or management in individual approval steps. Digitizing these processes without media discontinuity supports the verifiable execution of all activities, for example through electronic workflow signatures and audit-proof audit logs. "At the same time, the integration of all relevant stakeholders significantly increases process efficiency," says Schmeisser.
The security aspect of collaboration with external partners such as ICT service providers must also be taken into account. The exchange of sensitive information via email, including in the form of due diligence documents and cybersecurity questionnaires, represents attack vectors for cyberattacks and therefore a significant security risk. Schmeisser recommends collecting information and conducting contract negotiations in secure, digital rooms without the data leaving the protected environment.
What role do digital tools play in the implementation of DORA reporting obligations?
Both experts agree that the tasks that companies will have to perform as a result of DORA will be difficult to complete using manual methods. In addition to the enormous amount of work involved manually, there is a high potential for errors and the risk of incomplete documents and data when using the analog method. This needs to be avoided, especially when preparing for audit situations. Smart software that specializes in DORA, such as Fabasoft Dora, saves valuable resources, increases transparency, minimizes risks and ensures that information is always available for ad hoc requests.
Further details from the webinar can be found here in the full recording (only available in German).